Cyber Security Preview
PREVIEW:
Cyber Procedures to Tailor and Implement
The majority of businesses who suffer a cyber incident unprepared DO NOT survive. We need a higher level of understanding about Cyber security good practice.
View the Cyber Training & Awareness Videos Preview here.
Recommended Step by Step Process
This checklist will enable you to progressively adopt all recommended procedures. It helps you to demonstrate to stakeholders and regulators you have understood the Cyber Risks requirements as they apply to you, and provides a process for on-going Cyber Security compliance.

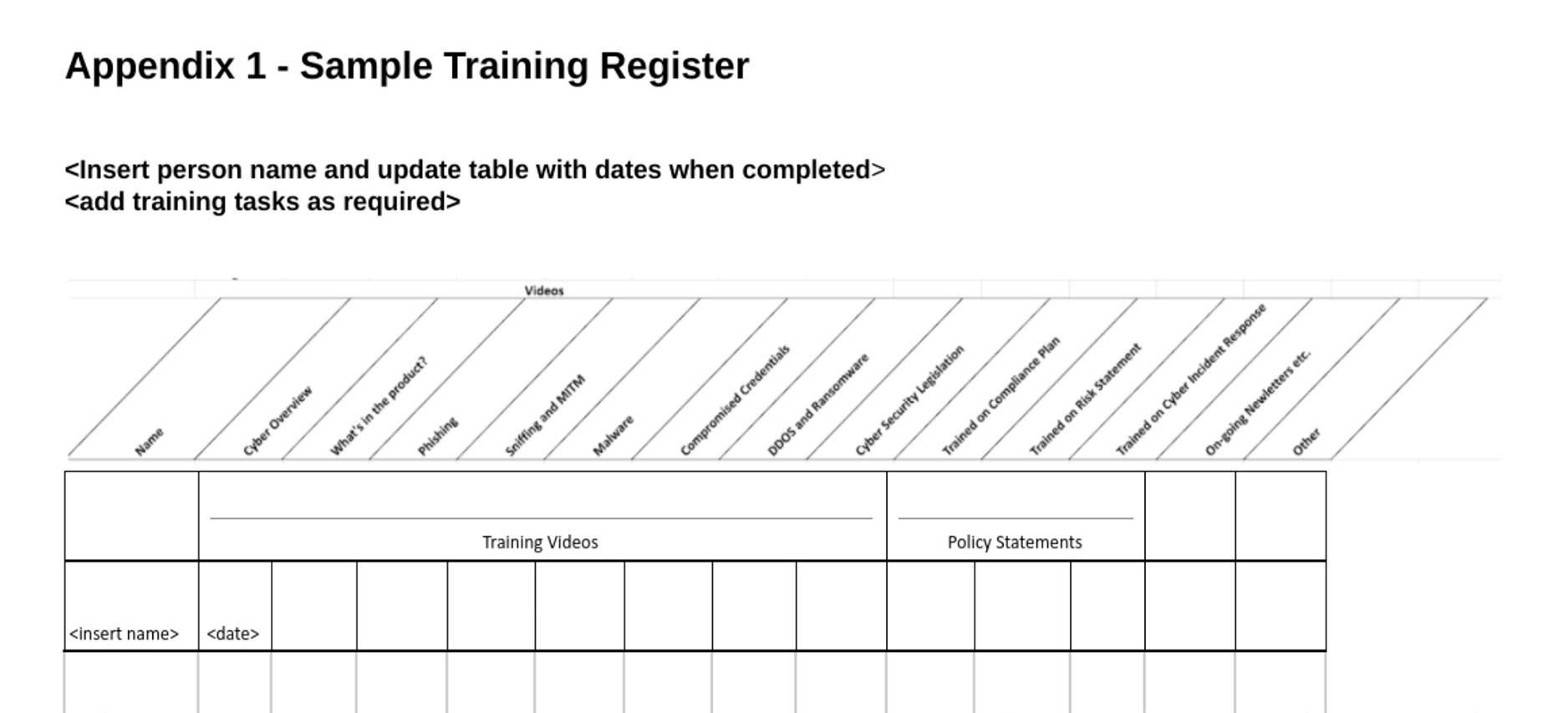
Staff training plan
The training plan provides a structure to analyse tasks performed, consider the level of cyber training required, record & monitor.
Good practice requires cyber risk awareness training of key threats, personal, regulatory and organisational responsibility, and mitigation.
Induction of new staff procedures
All new staff will undertake formal structured cyber induction training upon commencement, as well a continuing cyber training program. Details of induction training include keeping a register of systems accessed, issuing password policy and an acceptable use policy.

Induction of new customers and suppliers
Where functions are outsourced, processes for the selection and ongoing monitoring of external service providers will include consideration of their cyber security practices at the appointment stage. This allows you to monitor our cyber risk profile through that connection.
Staff exit process
For the purposes of cyber security there is an increased risk if an exit procedure is not carried out immediately. This policy will provide a structure to mitigate that risk.

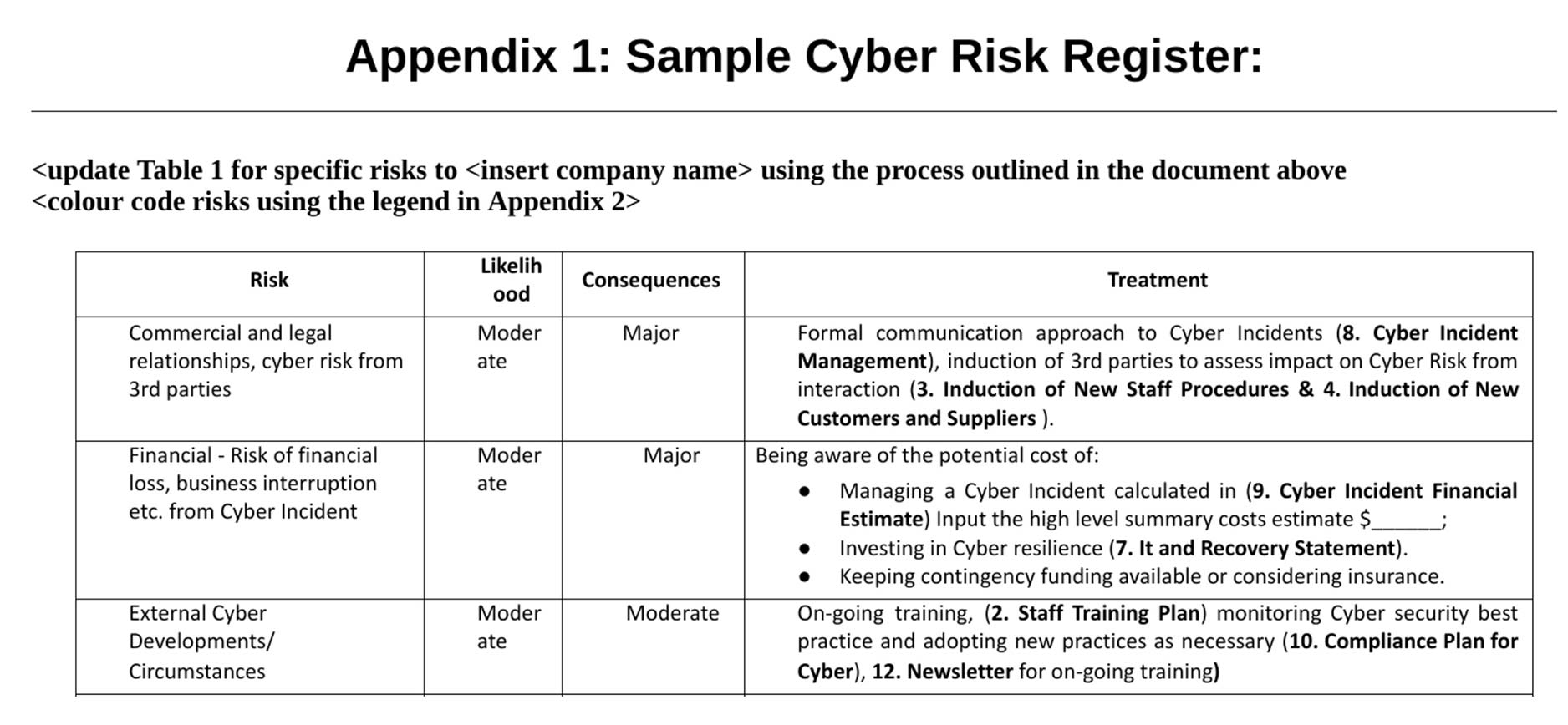
Risk management statement
Cyber risk exposures must be recognised, and then assessed for impacts based on clearly defined metrics such as response time, cost and legal or compliance implications. A risk plan can then be developed.
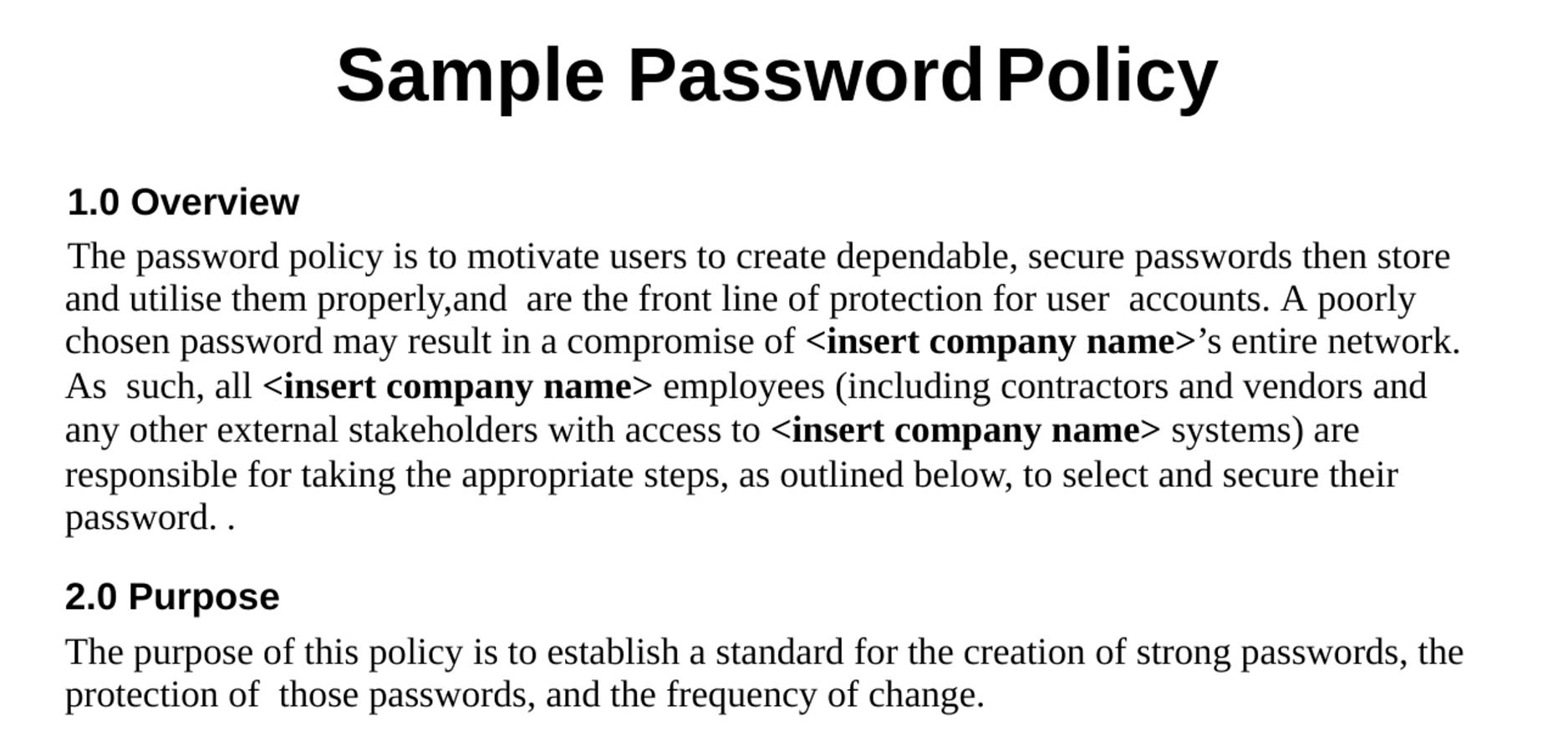
IT and recovery statement
This statement aims to reduce cyber risk by identifying and maintaining systems in use, eliminating threats, scheduling and running scans, documenting backup and restore routines, and other technology security processes.

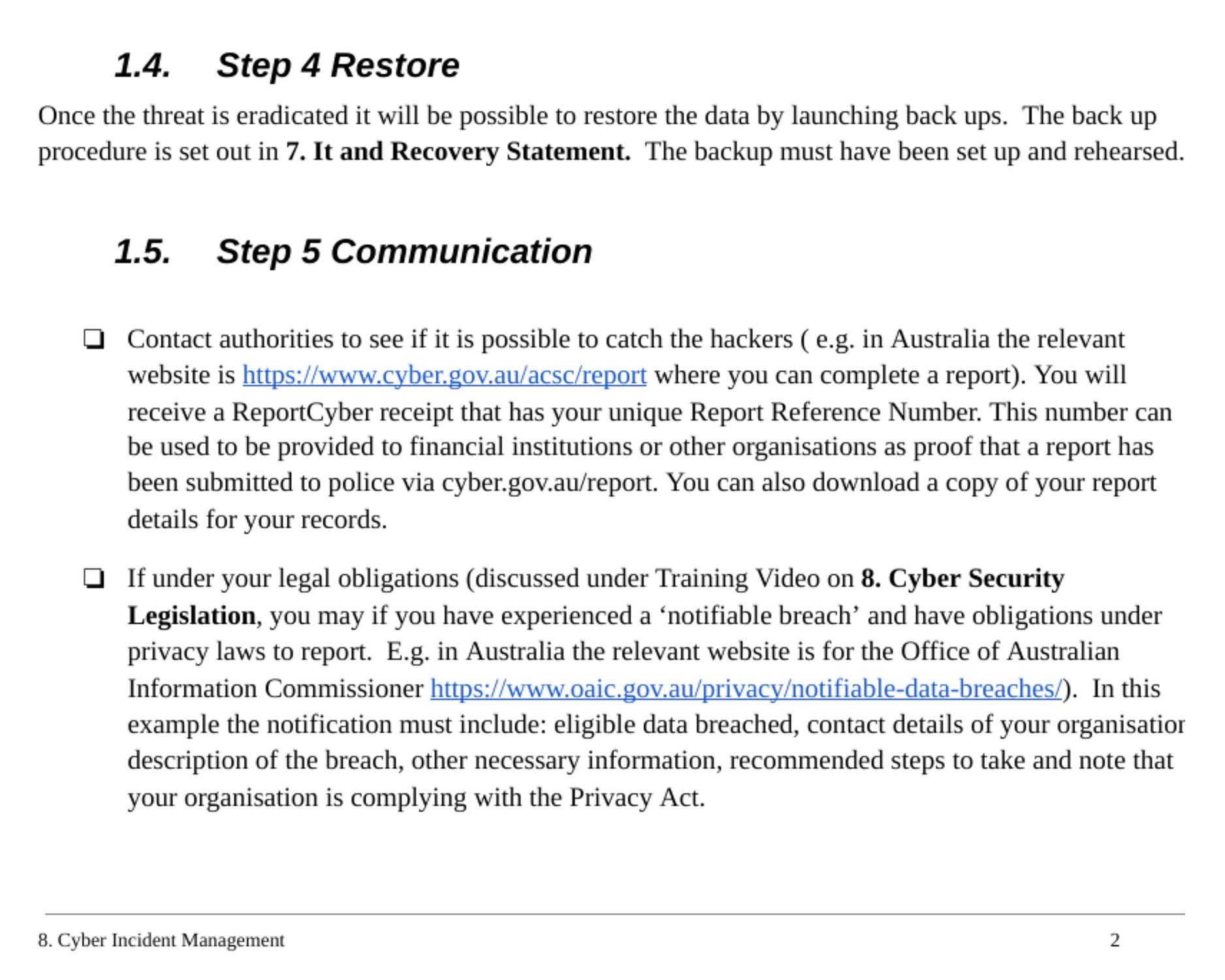
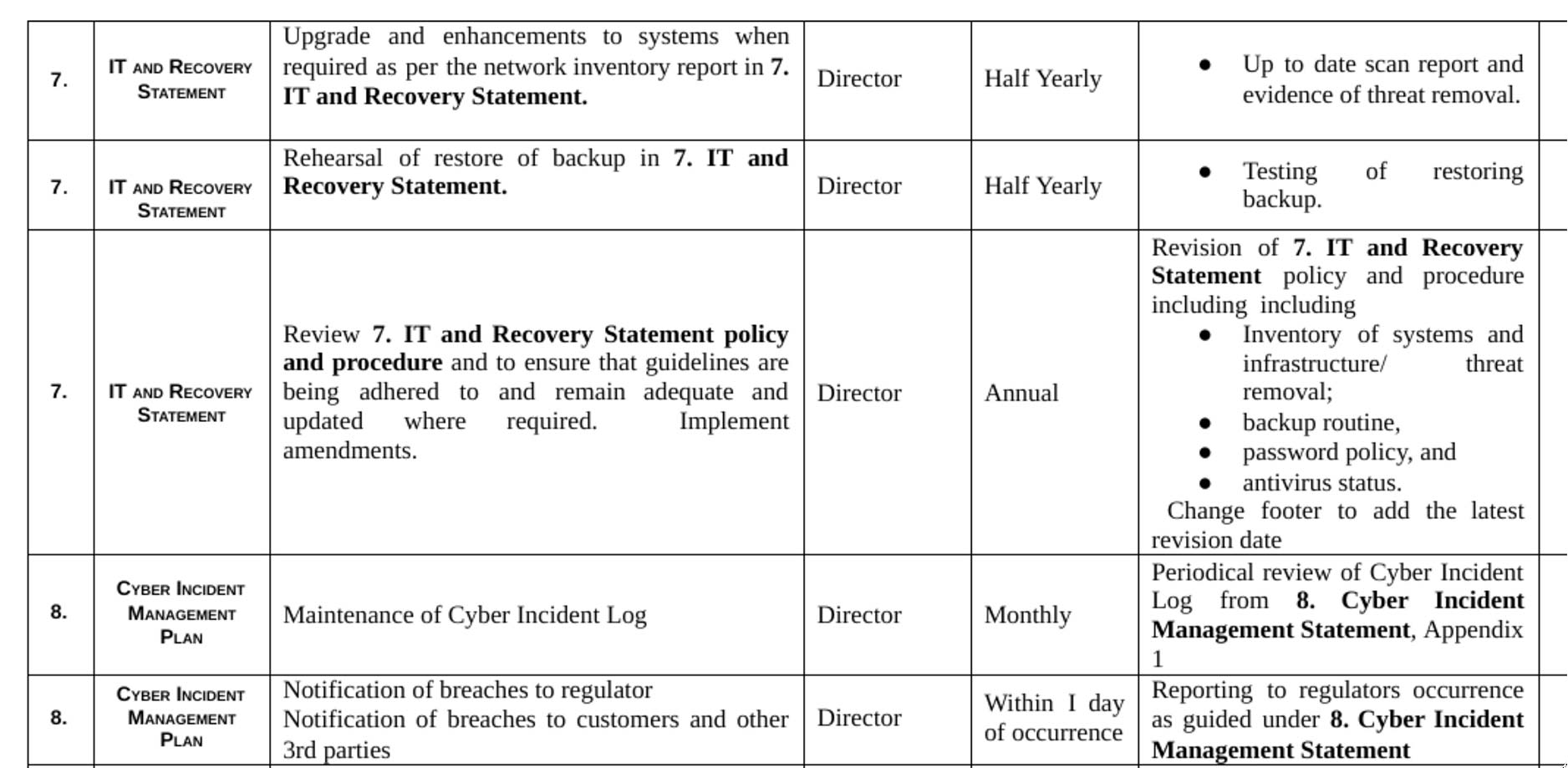
Cyber incident management
This statement is used to manage a Cyber Incident, and develop an actionable incident response plan. This includes having procedures for responding to and managing a cyber attack. It is a key part of cyber risk management for the organisation.
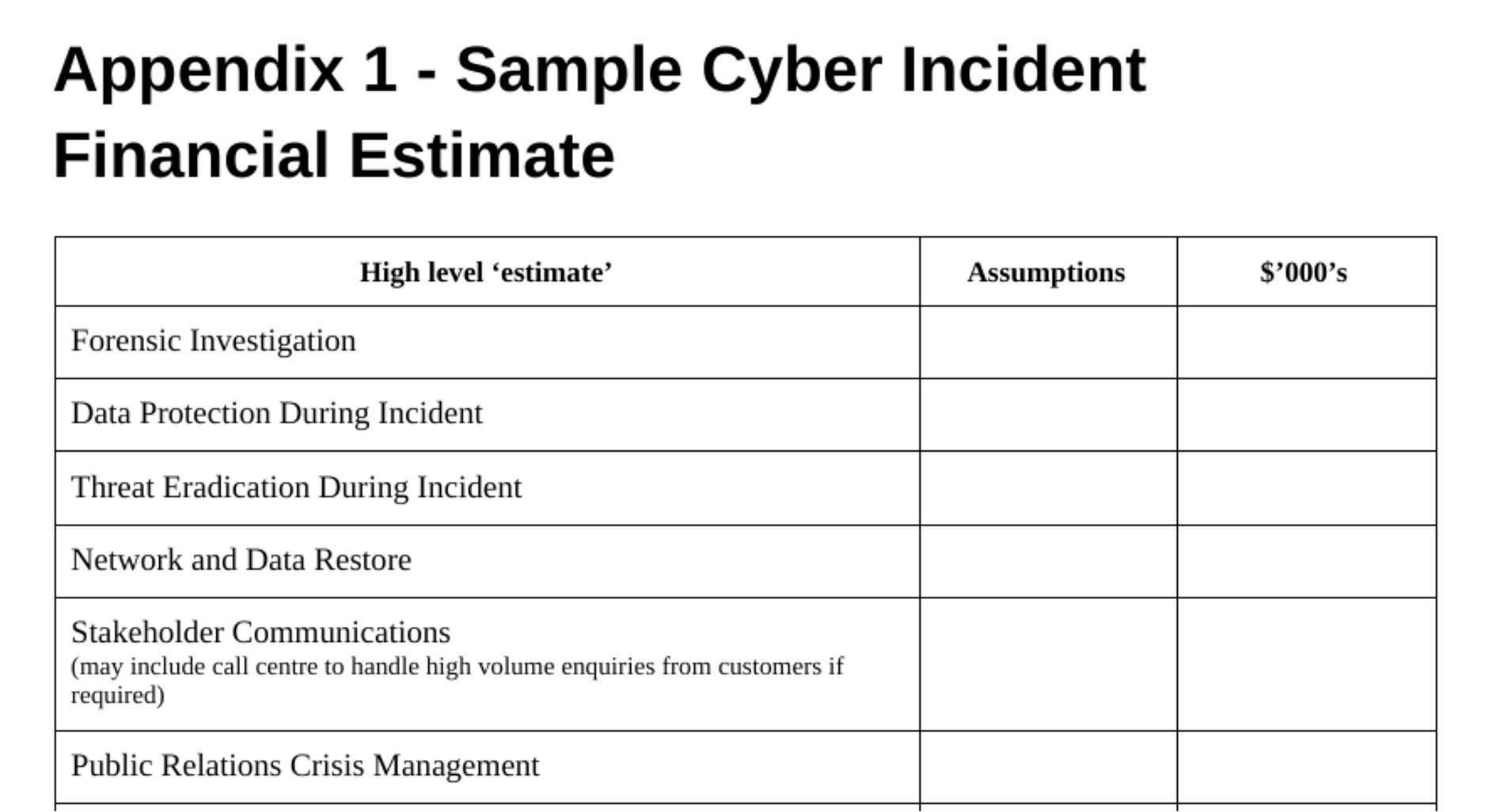
Cyber incident financial estimate
This statement is used to estimate financial risk from a Cyber Incident. An incident can lead to business interruption from computer system downtime, as well as the cost of regulatory investigations and fines. This can lead to a loss of profits, extra expense, and subsequent reputational harm.
Compliance plan for Cyber
This Compliance Plan for Cyber provides detail on:
- The Cyber Security measures and procedures in place;
- How compliance with those measures and procedures will be monitored.
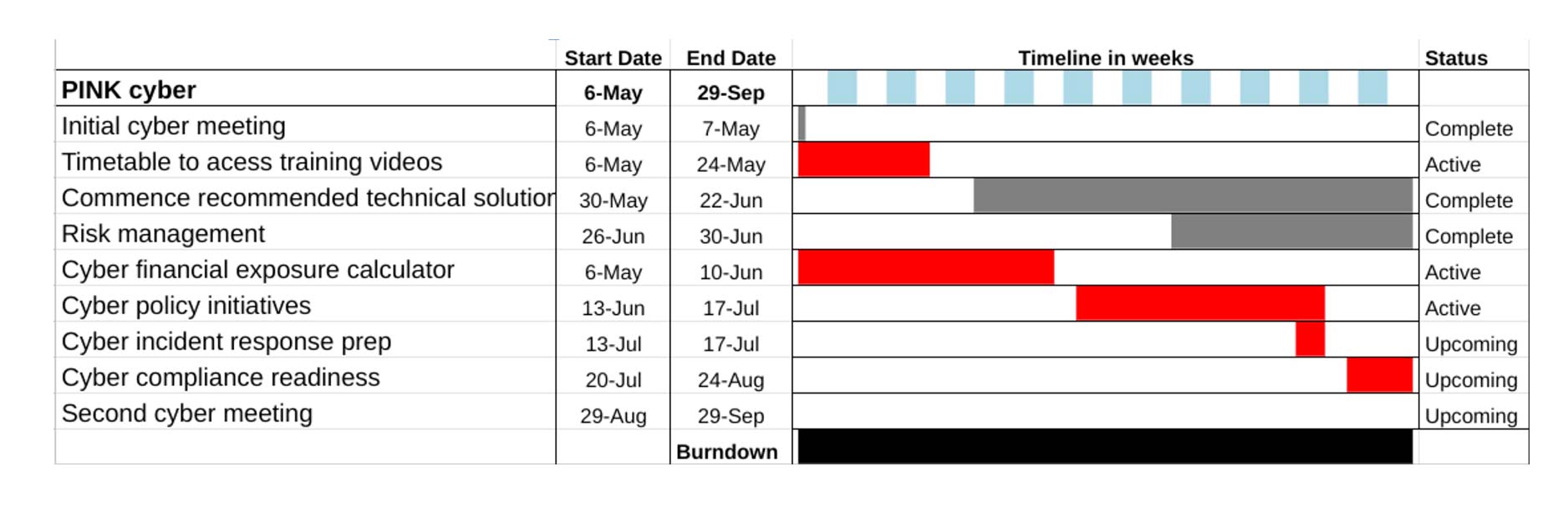
Cyber Tracker
This is a report which allows you to track progress towards your cyber security project at a glance.
Newsletter
Keep up to date in this dynamic area with regular newsletters on issues of practical importance.
Project Plan Outline
Update and prepare a Project Plan Outline for your team to work on implementing good Cyber security practice at your own pace.
View the Cyber Training & Awareness Videos Preview
Not sure which option is right for your business?
Contact us, we can help!